SOC 101 - A Brief Introduction to Security Operation Centers
The number of cyber attacks on public administrations, institutions and companies reported every month is increasing rapidly. This upward trend has been evident not only since the start of the Russian offensive against Ukraine, but is a result of increasingly professional hacker groups. In recent years, an increasingly profitable line of business has developed for cyber criminals. Attackers are increasingly resorting to extortion, even to the point of completely paralyzing the victims' IT systems. In this blog entry, I would like to explain to you what companies can do about this and how they can protect themselves.
One way companies can protect themselves against malicious cyber attacks is by using a Security Operation Center, or SOC for short. A Security Operation Center is a command center for IT security-related activities in a company. Here, individual systems are analyzed and operational and financial risks are identified. However, the work of a SOC is not purely preventive; it also actively detects ongoing cyber attacks and initiates possible mitigation measures.
A SOC consists of several components, which in turn cover different fields of activity. Basically, a SOC can be divided into four areas, as shown in the diagram below.
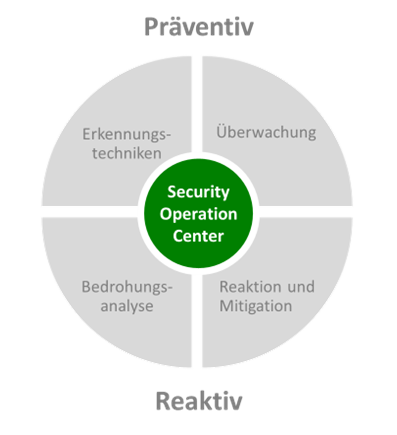
Depending on the size and type of company, the tasks and areas of the SOC can vary. Basically, it can be said that there is no such thing as the "one" Security Operation Center.
One of the most important tasks is the continuous monitoring of the company's own IT infrastructure, especially its network activities. This is done using previously defined policies as well as recognized best practices. Monitoring not only increases the detection rate of cyber threats, but also enables their timely mitigation. Cyber threats include not only actively ongoing attacks on the company, but also potential security risks and vulnerabilities in the company's own IT systems. Based on these findings, new threat scenarios can be derived in order to mitigate any previously undiscovered security risks or optimize the company's own security measures. All parts of the Security Operation Center work hand in hand to create a fully comprehensive security system.
After clarifying what exactly a Security Operation Center is and where its areas of responsibility lie, we will go into more detail about the implementation and deployment of a SOC in the upcoming blog entry. As soon as this is available, you will find the link here.
For more information on our cybersecurity services, please click here.
Author: Roman Scholtysik