Security Operation Center – Realization and Implementation
First, it is important to discuss what type of a Security Operation Center you would like to implement in your company. Because unfortunately, the principle that "there is no such thing as THE one Security Operation Center" also applies here. That is why a SOC is always individually tailored to your company. The Security Operation Center intervenes in all different areas of a company. Responsibilities of employees have to be redefined and new roles have to be defined and filled. The company-wide IT and Operational Technology (OT) infrastructure plays one of the most important roles in this context, because this is where the biggest changes and adjustments are made in an integrated SOC. Therefore, the first step before implementation and execution is to accurately determine the scope of a Security Operation Center.
Once the decision has been made that a Security Operation Center should be implemented and it is understood what changes will be coming to the company, the next question is "Where is our company secure and where do we see a need to catch up?" To answer this question, a look at the ISO27001:13 standard or the NIST Cyber Security Framework is helpful. These two frameworks are considered the most important foundations in the field of information security. Another method to determine protection goals is implementable with the help of risk management. We can warmly recommend the ISO27005 standard in this regard. In another blog post, we will go into more detail about the creation of an IT risk management system.
Now we come to another challenge in the creation of a Security Operation Center. The question of one's own risk tolerance (security), usability/flexibility and the costs incurred (costs). The diagram below illustrates this task.
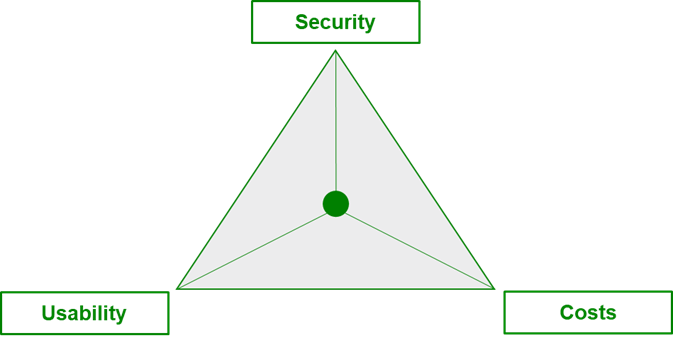
If a company has a particularly low risk appetite and wants to keep costs low in the process, then the flexibility of the company's IT and OT systems suffers, among other things. On the other hand, low costs and greater usability in a security operation center lead to increased security risks in the company. For an effective security operation center and thus containable information security, a balance between all three components is required. In our upcoming blog post, we will take a closer look at what such a balance might look like and how it relates to a security operation center.
Author: Roman Scholtysik