
Half a Year of War: Interim Analysis of the VOICE Cyber Security Competence Center (CSCC)
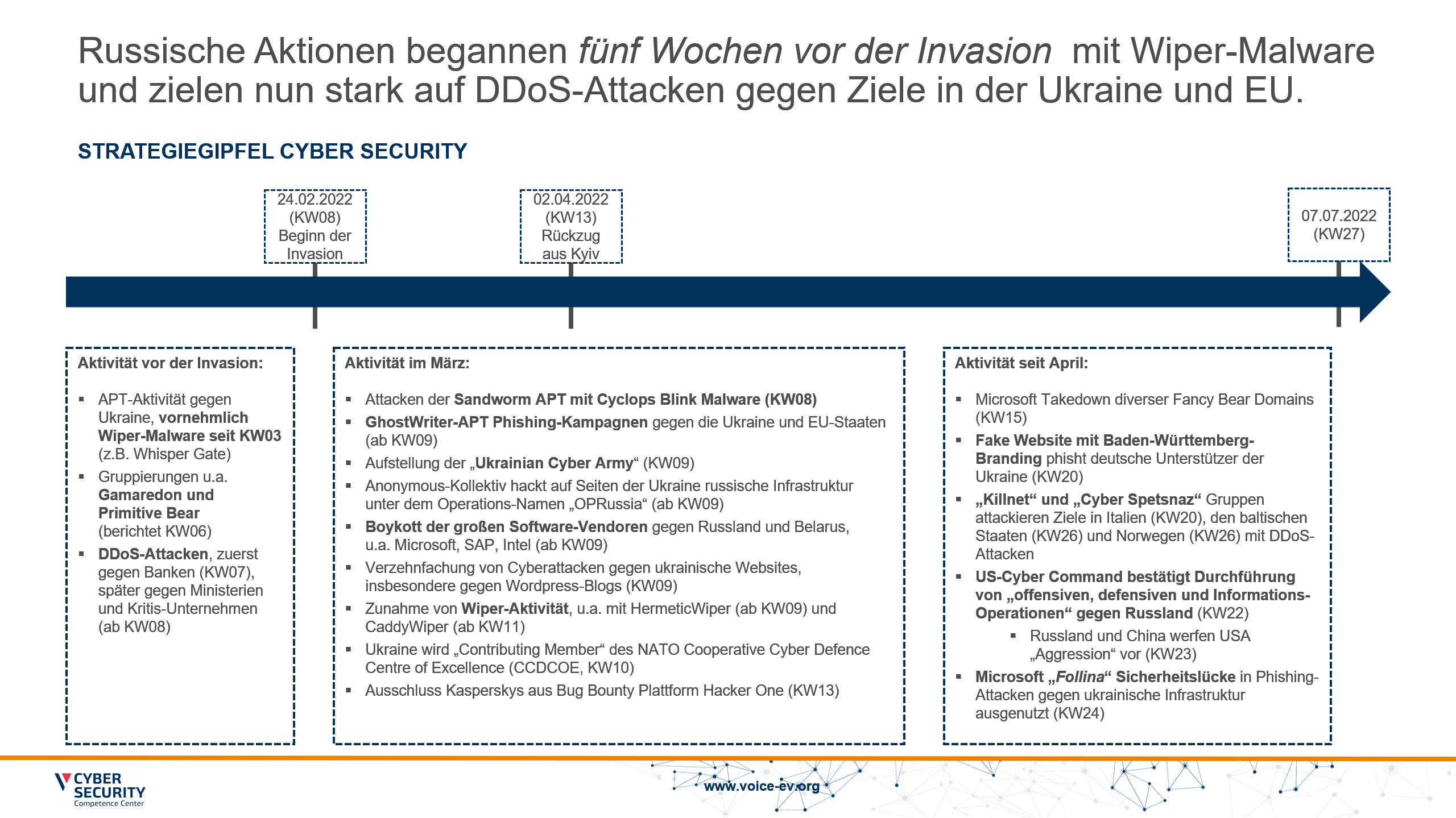
On Feb. 24, 2022, when the first bombs hit Kyiv and Russian tanks rolled across the Ukrainian border, a turning point occurred. The global security situation had abruptly changed from "extremely tense" to "most critical point since 1945." It was clear to all experts, even before the invasion, that cyber activities would play a significant role in the Russian war of aggression. However, how Russian network operations are shaping up has been observed by the CSCC over the past six months and discussed with companies in the community. What we found out is described in this blog post.
TL;DR: More activity than usual, but less than feared
Since the beginning of the year, Complion security experts at VOICE CSCC have reported on Russian and Belarusian activities in Ukrainian networks and in the EU. In particular, Wiper malware, a malware that deletes data, has been widely used by malicious actors since January 2022. Much of the Russian operations were low-complexity. Malware was mostly distributed via broad-based, shotgun-style phishing campaigns. This means that thousands of emails were sent simultaneously with particularly attention-grabbing subjects - examples include fake notifications from the EU or fake news about possible nuclear strikes by Russia. In addition to the use of wiper malware, strong DDoS campaigns were also conducted against Ukraine's critical infrastructure (esp. the financial sector and government agencies) in order to inhibit the flow of information on the Ukrainian side.
In addition, free riders were mixed into the increased background noise caused by the cyber activities, which, for example, operated crypto fraud with alleged fundraising. Within the CSCC community, the growing cyber activity was measured by increased port scanning. However, direct attacks were not recorded by the participating companies.
Wipers as far as the eye can see
One malware class that stood out in the first weeks of the war was so-called wiper malware. This deletes data either completely or partially to a degree that makes recovery impossible. The first Wiper operations were made public by Microsoft as early as 13.01.2022. Here, the Whisper Gate malware was used against Ukrainian critical infrastructure. Later, other wipers were added, such as the HermeticWiper and the CaddyWiper. With the official start of the war on February 24th, the number and activity of the wipers also increased sharply.
External assistance to Ukraine
While arms shipments and other aid were delayed, cyber support for Ukraine came at breakneck speed. Across the Atlantic, major vendors, such as Microsoft and Cisco, as well as U.S. intelligence agencies, worked diligently to provide intelligence and defensive technologies against Russian and Belarusian hacking attacks. For example, Cisco deployed several hundred security experts to harden Ukrainian government networks, and U.S. Cyber Command reported it had been conducting offensive and defensive "information operations" on the network against Russia since the war began.
Ukraine received special help from the hacker collective Anonymous, which for the most part backed the country, and from the Ukrainian Cyber Army, a non-organizational group of hackers that conducted astonishingly effective cyber operations against Russian government and critical systems.
A lot of saber rattling, no complex attacks - but why?
What we observed against Ukrainian networks (and partly against the West) were low-complexity attacks. These included the aforementioned wiper and DDoS attacks, but defacement actions, in which websites are flooded with Russian propaganda, have also been commonplace since the beginning of the year.
What was missing were complex cyberattacks that left lasting damage. This is due in particular to the fact that such operations involve enormous amounts of time and tend to devour massive amounts of resources. The best example of this was the Stuxnet attack against Iran's nuclear program in 2010. The worm that attacked the centrifuges took five years to develop with the cooperation of three intelligence agencies. The attack vector was the physical insertion of the malware via USB stick by a collaborator.
All of this is neither possible nor necessary in a more or less classic war of combat, such as the one Russia is currently waging against Ukraine. The fog of war makes enemy reconnaissance difficult, and Russian hackers are busy defending their own networks. That leaves little capacity for sophisticated operations. At the same time, if one is already in open conflict, it is far more efficient to use ballistic weapon systems. First, because the use of conventional weapons requires far less reconnaissance time and expertise, and second, because in most cases the impact of a cruise missile has a more devastating effect against the target - both physically and morally. A destroyed factory is more tangible to the population than the deletion of system data of a production line.
For the remainder of the war, unless events on the battlefield fundamentally change, complex cyber operations will continue to be unlikely. Nonetheless, the disruptive effects of information warfare are more likely to intensify than to abate.
The VOICE CSCC with Complion's cybersecurity experts n will continue to report on the situation and provide relevant information to the CSCC community.
If you would like to become part of the CSCC community, please contact voice-info@voice-ev.org.
If you want to join our team, please have a look at our career page.
Author: Tobias Philipsen