
KIA Hacking - Vulnerability in web portal allows takeover of cars
In June, security researchers discovered serious security vulnerabilities in Kia's dealer infrastructure. Just by knowing license plates, they were able to locate, open, lock, start, stop and operate the horn on more than 500 vehicle models. They were also able to exfiltrate the personal data of vehicle owners. Read this blog post to find out how this was possible and why such findings could occur more and more frequently in the future.
The current case of a theoretical Kia hack
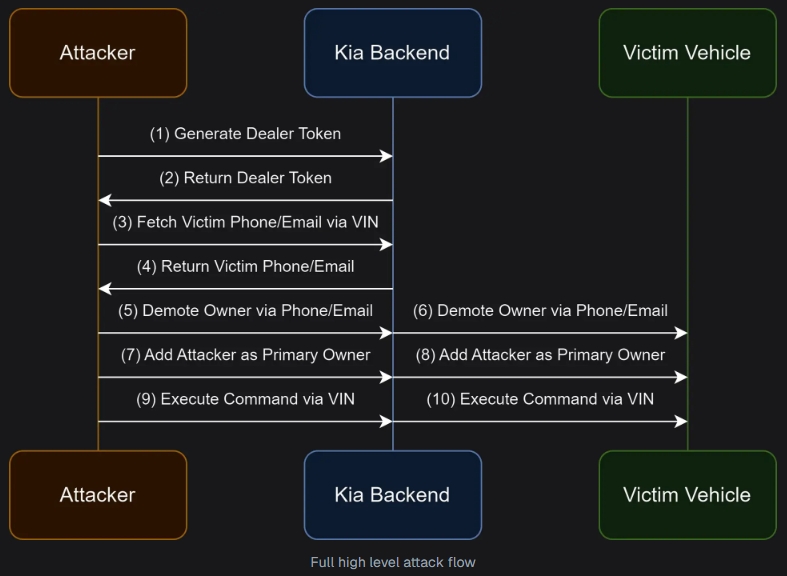
Security researchers led by Sam Curry discovered vulnerabilities in the portals and vehicles of several manufacturers back in 2022. Two years later, they decided to look for loopholes again. Their first focus was on Kia. After analyzing the vehicle owner portal, the group focused on the web portal for Kia dealers. Using an invitation link, they were able to create an account for a fictitious dealership and then retrieve the data of any user accounts (names, telephone numbers, email addresses). To do this, the attackers only needed to know the license plate number and the country in which the car was registered.
With the combination of account information and vehicle data, the attackers were able to demote the actual owner and register themselves as the vehicle owner with an email address of their choice. The group led by Sam Curry was then able to unlock and start the car using a self-programmed tool. The hackers were also able to operate the horn. All of this was tested with a rented Kia EV6. In a fictional "access scenario", the hackers could theoretically have forced a moving Kia to stop. The security gaps were communicated to the vehicle manufacturer and closed in July 2024.
A smarter world with increased risks
The director of CISA, Jen Easterly, recently drew a comparison between software and a car during a public appearance. It is acceptable to use software that will be supplied with security patches for several years after its initial release. However, no one would get into a car that might have bugs that would impair driving ability or safety.
According to Easterly, software developers should take their cue from the manufacturers of cars and airplanes. However, the example of Kia (which is certainly not alone - it could have been any other brand) shows us that the opposite is more likely to be the case. Cars will come with tons of software and this software will inevitably contain bugs that can be exploited by malicious actors. This won't stop anyone from getting in a car and driving off, but the reality that cars are moving IoT devices should not be ignored. So manufacturers need to work productively with white hat hackers, issue bug bounties and close security gaps quickly and regularly. According to Sam Curry, Kia has done an exemplary job here.
Author: Tobias Philipsen