Selection of a suitable information security standard from the perspective of small and medium-sized enterprises (SMEs)
What is information?
Information is the heart of a company. Information is all data that keeps the organism company alive. This data includes, for example, the company's own business secrets, the salary data of its employees, system information, but also the telephone call between the purchaser and the supplier.
In short, information is all types of data in a company that have a certain value and are more or less decisive for the continued existence of companies or the functioning of business processes and must therefore be protected. Information can be analog, digital, structured, unstructured, physical or meta-physical.
What is information security?
The term information security is not clearly defined in the literature. In some cases, for example, people use it synonymously with terms such as IT security and cybersecurity. For the purposes of this blog post, we will use one of the more familiar definitions: Information security protects information in terms of its confidentiality, integrity and availability using appropriate measures.
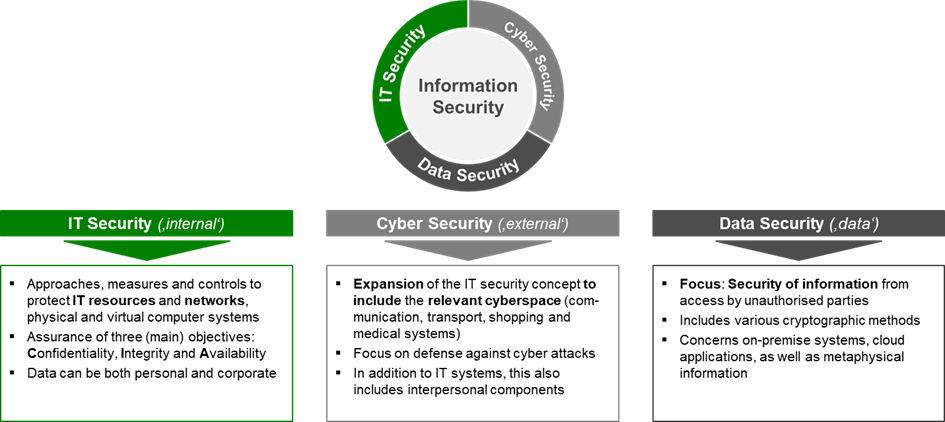
However, it must be borne in mind that information security is not a rigid concept. No information can be declared secure according to objective standards, but only in consideration of the context in which it is viewed. Information that was considered to be well protected more than 1-2 years ago can easily be stolen today.
In addition to this fluidity of the term itself, the requirement for information security differs from company to company. Information that may seem unimportant to one company is considered critical by others, and its loss could have far-reaching consequences. Furthermore, internal company factors always have an influence on how information security can be practiced in one's own company.
Does my company have an information or IT security department? How many employees in my company can deal with information security? Are they appropriately trained and educated? What budget do I have to use technical systems for automated monitoring?
All these factors, whether organizational, personnel, professional or technical, have an influence on how information security can be implemented in my company.
How do I implement information security in my company?
Just as there is no global answer to the question of what information security is, there is no universal answer to the question of how to implement it in your own company. Nevertheless, some methods have emerged over time that can help companies make the implementation of information security visible and verifiable.
One of these options is the introduction of information security management systems (ISMS). This is a company-wide tool that combines policies, procedures, guidelines, resources, and activities in the area of information security. The goal is to introduce the individual components, implement them, apply them in operation, monitor their functionality, review them and, if necessary, optimize them.
In addition to an ISMS, there are other ways to implement information security and, in particular, to provide evidence of its implementation. Unlike these methods, however, an ISMS has a decisive advantage. If implemented correctly, information security becomes anchored in management at an early stage. In practice, this awareness is often lacking in other information security projects, but it often determines their success or failure.
So which information security standard is right for me?
Unfortunately, there is no one-size-fits-all answer here either. First and foremost, it is necessary to know your own company. One approach is to first determine the necessary assets and resources based on the company's own business processes. On this basis, the most important information in a company can be deduced (the so-called crown jewels).
Once this information is available, you can start researching a suitable information security standard. The following questions in particular should be considered:
- Is the standard suitable for the complexity of my company? (For example, is it aimed at SMEs or corporate groups?)
- Does an industry standard already exist for my company? (e.g. PCI DSS v4.0, B3S, HITRUST, NIST CSF)
- Does my company operate internationally and should certification, for example, be recognized internationally? (National vs. international standards)
- Are there specific requirements as to which areas are to be secured and how extensive the implementation of information security should be? (Transition standards such as VdS 10000 and CISIS12 vs. ISO/IEC 27001 or BSI IT-Grundschutz)
- Do individual factors exist that I should consider in the selection process? (Projected company growth, budget for implementation and operation of information security processes, innovations/adaptations in the IT portfolio)
- What risks do I anticipate in my business and what risks am I willing to bear? (Risk assessment and risk appetite)
To name just a few. Based on these questions, the number of suitable standards often shrinks. Based on this curated selection, a more in-depth analysis of the individual candidates can then take place.
Here, it is advisable to use a combination of SWOT analysis and pro-con lists to compare standards with each other and to make synergy effects visible. For example, it is conceivable to use the extensive catalog of BSI IT-Grundschutz to simplify the implementation of ISO/IEC 27001. On the other hand, it may also make sense to implement transitional standards such as CISIS12 in order to facilitate the later introduction of "full-value" standards.
You can then use the results to develop weighted decision trees to make the selection process more transparent and to integrate your own management into the decision-making process.
We would be happy to support you in finding and implementing the right standard for your company.
Author: Robin Enste