Cybersecurity October Review: Zero-Day Vulnerabilities in Microsoft Exchange Servers
In early October, reports became public about two vulnerabilities in Microsoft Exchange Server 2019, 2016, 2013 - an email server software widely used in enterprises. To exploit them, malicious actors chain both vulnerabilities together. Thus, they can execute malware on Exchange Server to move further into the network, exfiltrate and/or encrypt data. In addition to the severity of the vulnerability, the problem is that malicious actors, presumably a state-sponsored organization, identified and exploited it before Microsoft did. Microsoft has not yet provided any updates, which means that IT administrators can only implement a workaround. However, this has now been exposed as ineffective once again. Indicators of compromise are also known. These are patterns that can be used to search log files and prove that you have been affected.
What is the problem?
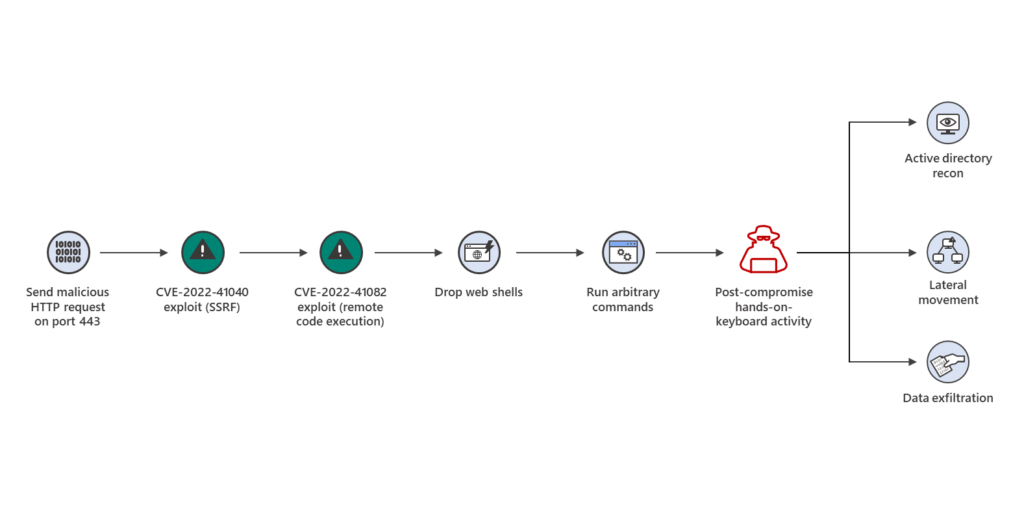
To chain and exploit the vulnerabilities, attackers first send a malicious http request to an Exchange server. This is intended to exploit a Server Side Request Forgery vulnerability (CVE-2022-41040) to elevate the attackers' privileges. With elevated privileges, the remote code execution vulnerability (CVE-2022-41082) is exploited. This means attackers can implement malicious scripts on the server to move further in the network, exfiltrate and/or encrypt data.
Thus, they can execute malicious scripts on the Exchange Server to move further in the network, exfiltrate and/or encrypt data.
Why is it a problem?
Besides the severity of the vulnerability, it is problematic that malicious actors have already identified and exploited it before Microsoft. According to the manufacturer, this is supposed to be a state-supported organization. Microsoft has not released any updates yet, which will close the vulnerability.
What should you do?
IT administrators should implement mitigation measures as soon as a working workaround is communicated again. In addition, Indicators of Compromise are known, basically patterns that can be used to search through IIS log files and ensure one's own concern.
All current developments on this and other cybersecurity topics are discussed weekly by Complion's experts in the Trusted Community of the Voice Cyber Security Competence Center.
Author: Jan-Hendrik Butt